Table Of Content

It contains the real implementation of the business logic or the resource that the client code wants to access. A real-world example can be a cheque or credit card as a proxy for what is in our bank account. It can be used in place of cash and provides a means of accessing that cash when required. Create an interface with the name ISharedFolder.cs, and then copy and paste the following code. This interface defines the common methods the Real Object and the Proxy class will implement.
The Proxy Design Pattern in Java
The Proxy Method Design Pattern in Java is a valuable tool for enhancing control, security, and performance in software systems. When applied correctly and carefully, this pattern provides a modular and flexible approach to extending or modifying the behavior of objects. The pattern provides an effective mechanism for controlling access, optimizing performance, and adding functionalities without directly altering the original object. We have to create a simple banking application with a proxy to control access to the real bank account. For a more general introduction to design patterns, refer to this overview article, which is an excellent starting point for exploring the fascinating world of software design patterns.
Step 2: Implement the Real Object
In simple terms, the Proxy Pattern is like having a middle person (proxy) who decides when to get help from the real expert (real object) and when to handle things themselves. It’s a way to manage and control access to someone’s skills without bothering them unnecessarily. Knowing how to efficiently access those resources while providing appropriate access control is therefore crucial for building scalable and secure applications.
Protection proxy
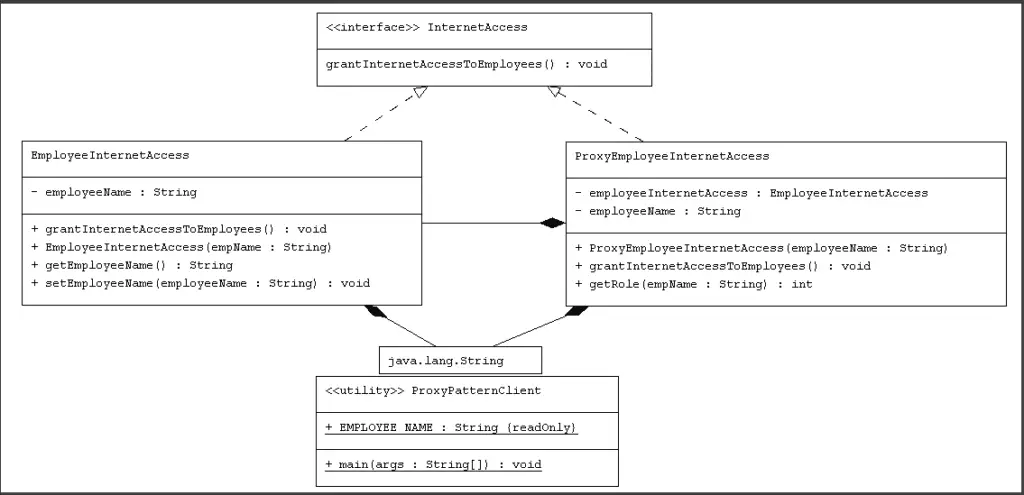
The local object is a proxy for the remote object, and method invocation on the local object results in remote method invocation on the remote object. An example would be an ATM implementation, where the ATM might hold proxy objects for bank information that exists in the remote server. What we can do here is, in between the employees and the shared computer, we need to introduce the Folder Proxy.
The System Design Cheat Sheet: Load Balancer, Reverse Proxy, Forward Proxy, API Gateway - hackernoon.com
The System Design Cheat Sheet: Load Balancer, Reverse Proxy, Forward Proxy, API Gateway.
Posted: Wed, 30 Aug 2023 07:00:00 GMT [source]
Diagrammatical Representation of the Proxy Method Design Pattern in Java
Best of 2023: Top 9 Microservices Design Patterns - Cloud Native Now
Best of 2023: Top 9 Microservices Design Patterns.
Posted: Wed, 03 Jan 2024 08:00:00 GMT [source]
Let’s delve into the world of the Proxy Design Pattern, learn how to use it in Python, discover its pros and cons, and look at its usage in the Python standard library. A user shouldn’t be able to change person’s age to a string value, or give them an empty name. Or if the user is trying to access a property on the object that doesn’t exist, we should let the user know.
This is when you need to be able to dismiss a heavyweight object once there are no clients that use it. The client code (ProxyPatternExample) demonstrates the usage of the Proxy Design Pattern. It creates an Image object, which is actually an instance of ProxyImage. The Client will use the Proxy Object, and the Proxy object will call the Actual Object behind the scenes. In our example, the Main Method of the Program class is going to be the Client, So Please modify the Main method of the Program class as shown below. ProxyPatternDemo, our demo class, will use ProxyImage to get an Image object to load and display as it needs.
Relations with Other Patterns
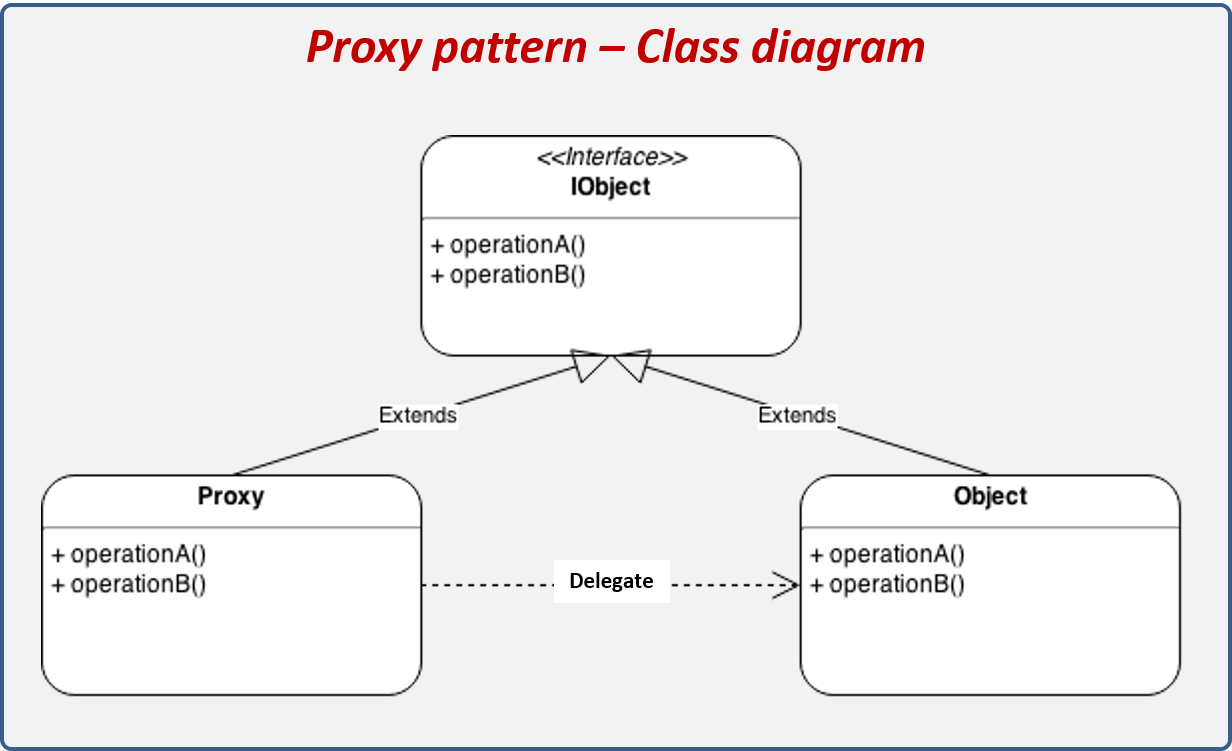
In essence, the Proxy Design Pattern involves creating a new proxy class as an interface for the actual class. This pattern is a type of structural design pattern as it’s concerned with how classes and objects can be composed to form larger structures. The Proxy Design Pattern introduces a layer of protection to the actual object from the outside world. This is particularly useful when the original object is vulnerable, or complex and heavy. The Image interface declares the common methods for displaying images, acting as a blueprint for both the real and proxy objects.
Proxy (ProxyImage Class):
A better solution would be to display images only when actually needed. In this sense, we can use a proxy to wrap the existing ImageViewer object. This way, the actual image viewer will only get called when the image needs to be rendered. If we assume there exists a class, ImageViewer, responsible for loading and displaying images - we might implement our file manager by using this class directly. This kind of approach seems logical and straight-forward but it contains a subtle problem.
By applying the Proxy pattern, we can create a proxy with the same interface as the real report generator object The UI keeps interacting with the proxy. It is only when the UI asks the proxy to generate a report, the proxy will instantiate the real report generator object. Such proxy is called virtual proxy – It creates expensive objects on demand.
An excellent real-world example of the Proxy Design Pattern in the Python Standard Library is the weakref module. A weak reference is a pointer to an object that doesn't prevent the object from being garbage collected. Hence, it's a kind of proxy that references the original object without preventing it from dying. To act as substitute for a subject, a proxy must implement the Subject interface.Clients can't tell whether they work with a subject or its proxy.
Until then, no images will be loaded or processed, which will make our program much more efficient. The Proxy Design Pattern is a design pattern belonging to the set of structural patterns. Structural patterns are a category of design patterns used to simplify the design of a program on its structural level. In place of a complex or heavy object, a skeleton representation may be advantageous in some cases. When an underlying image is huge in size, it may be represented using a virtual proxy object, loading the real object on demand. In the above UML class diagram, the Proxy class implements the Subject interface so that it can act as substitute for Subject objects.
And if everything is fine, the bank employee gives the required money to Anurag. According to the Gang of four definitions, the Proxy Design Pattern provides a surrogate (act on behalf of another) or placeholder for another object to control access to it. In proxy pattern, we create object having original object to interface its functionality to outer world. In the ReportGeneratorImpl class above, we wrote very simple method implementations of the ReportGenerator interface. We have even left the displayReportTemplate() method empty, as we would like the proxy to implement it. To apply the Proxy pattern to our report viewer example, we will first write the ReportGenerator interface, which is the Subject.
As an example, In Spring AOP you create proxies of the objects that handle the cross cutting concern code. The Proxy pattern also forms the core foundation of remoting technologies that Spring supports, such as RMI, Spring’s HTTP Invoker, Hessian, and Burlap. Through the use of a proxy, the upstream software is unaware it is using a remoting technology.
In this design, it defines the display() method that both RealImage and ProxyImage must implement. This ensures a uniform interface for clients interacting with image objects. The Proxy pattern suggests that you create a new proxy class with the same interface as an original service object. Then you update your app so that it passes the proxy object to all of the original object’s clients. Upon receiving a request from a client, the proxy creates a real service object and delegates all the work to it.

No comments:
Post a Comment